Permission manager : RBAC management for Kubernetes

Came across a GitHub repository implemented by the awesome folks at Sighup.IO for managing user permissions for Kubernetes cluster easily via web UI.
GitHub Repo : https://github.com/sighupio/permission-manager
With Permission Manager, you can create users, assign namespaces/permissions, and distribute Kubeconfig YAML files via a nice&easy web UI.
The project works on the concept of templates that you can create and then use that template for different users.Template is directly proportional to clusterrole.
In rder to create a new template you need to defile a clusterrole with prefix template-namespaces-resources__. The default template are present in the k8s/k8s-seeds directory.
Example template:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: template-namespaced-resources___developer
rules:
- apiGroups:
- "*"
resources:
- "configmaps"
- "endpoints"
- "persistentvolumeclaims"
- "pods"
- "pods/log"
- "pods/portforward"
- "podtemplates"
- "replicationcontrollers"
- "resourcequotas"
- "secrets"
- "services"
- "events"
- "daemonsets"
- "deployments"
- "replicasets"
- "ingresses"
- "networkpolicies"
- "poddisruptionbudgets"
# - "rolebindings"
# - "roles"
verbs:
- "*"
Let us now deploy it on Katakoda kubernetes playground and see the permission checker in action.
Step1: Open https://www.katacoda.com/courses/kubernetes/playground
Step 2: git clone https://github.com/sighupio/permission-manager.git
Step3: Change the deploy.yaml file
master $ kubectl cluster-info
Kubernetes master is running at https://172.17.0.14:6443
update the deployment file “k8s/deploy.yaml” with the CONTROL_PLANE_ADDRESS from the result of the above command.
apiVersion: apps/v1
kind: Deployment
metadata:
namespace: permission-manager
name: permission-manager-deployment
labels:
app: permission-manager
spec:
replicas: 1
selector:
matchLabels:
app: permission-manager
template:
metadata:
labels:
app: permission-manager
spec:
serviceAccountName: permission-manager-service-account
containers:
- name: permission-manager
image: quay.io/sighup/permission-manager:1.5.0
ports:
- containerPort: 4000
env:
- name: PORT
value: "4000"
- name: CLUSTER_NAME
value: "my-cluster"
- name: CONTROL_PLANE_ADDRESS
value: "https://172.17.0.14:6443"
- name: BASIC_AUTH_PASSWORD
valueFrom:
secretKeyRef:
name: auth-password-secret
key: password
---
apiVersion: v1
kind: Service
metadata:
namespace: permission-manager
name: permission-manager-service
spec:
selector:
app: permission-manager
ports:
- protocol: TCP
port: 4000
targetPort: 4000
type: NodePort
Step4: Deploy the manifests
cd permission-manager
master $ kubectl apply -f k8s/k8s-seeds/namespace.yml
namespace/permission-manager created
master $ kubectl apply -f k8s/k8s-seeds
secret/auth-password-secret created
namespace/permission-manager unchanged
clusterrole.rbac.authorization.k8s.io/template-namespaced-resources___operation created
clusterrole.rbac.authorization.k8s.io/template-namespaced-resources___developer created
clusterrole.rbac.authorization.k8s.io/template-cluster-resources___read-only created
clusterrole.rbac.authorization.k8s.io/template-cluster-resources___admin created
rolebinding.rbac.authorization.k8s.io/permission-manager-service-account-rolebinding created
clusterrolebinding.rbac.authorization.k8s.io/permission-manager-service-account-rolebinding created
serviceaccount/permission-manager-service-account created
clusterrole.rbac.authorization.k8s.io/permission-manager-cluster-role created
customresourcedefinition.apiextensions.k8s.io/permissionmanagerusers.permissionmanager.user created
master $ kubectl apply -f k8s/deploy.yaml
deployment.apps/permission-manager-deployment created
service/permission-manager-service created
Step5: Get the NodePort and open UI using Katakoda
master $ kubectl get svc -n permission-manager
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
permission-manager-service NodePort 10.104.183.10 <none> 4000:31996/TCP 9m40s
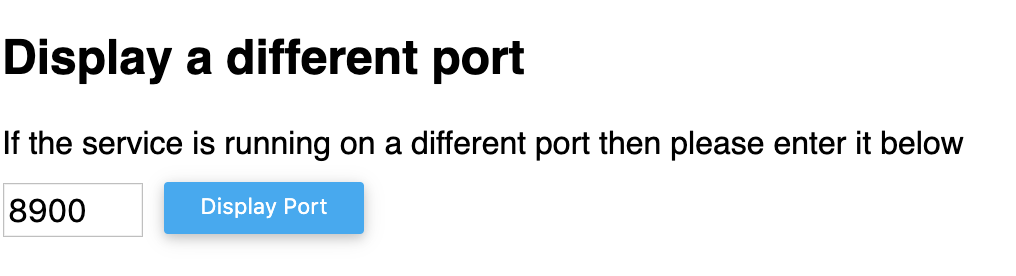
n order to open port from Katakoda click on the + and select View HTTP port 8080 on Host 1 and change the port to 31996
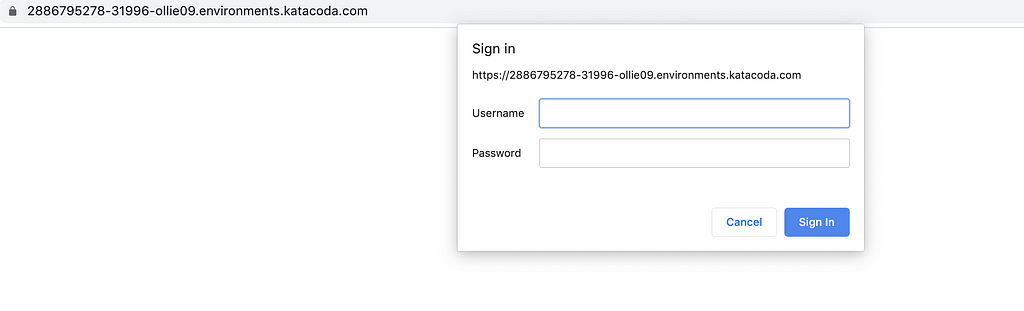
Enter the username and password :
username: admin
password: 1v2d1e2e67dS
You can change the password in k8s/k8s-seeds/auth-secret.yml file.
Now Let us create some users and assign one of the default template.
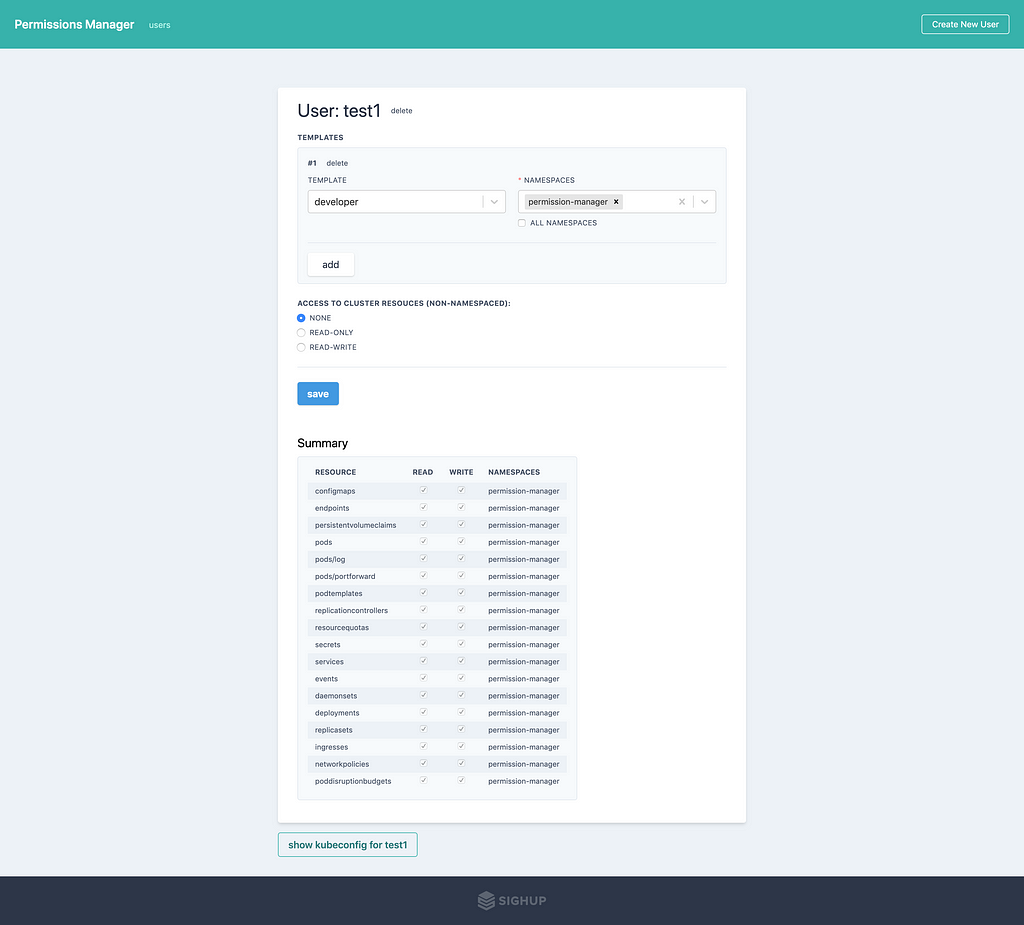
Let us download the kubeconfig file and test the permissions:
master $ kubectl --kubeconfig=/root/permission-manager/newkubeconfig get pods
Error from server (Forbidden): pods is forbidden: User "test1" cannot list resource "pods" in API group "" in the namespace "default"
master $ kubectl --kubeconfig=/root/permission-manager/newkubeconfig get pods -n permission-manager
NAME READY STATUS RESTARTS AGE
permission-manager-deployment-544649f8f5-jzlks 1/1 Running 0 6m38s
master $ kubectl get clusterrole | grep template
template-cluster-resources___admin 7m56s
template-cluster-resources___read-only 7m56s
template-namespaced-resources___developer 7m56s
template-namespaced-resources___operation 7m56s
Summary: With permission checker you can easily create multiple users and give permission for specific resources in specific namespace using custom-defined templates.
About Saiyam
Saiyam is a Software Engineer working on Kubernetes with a focus on creating and managing the project ecosystem. Saiyam has worked on many facets of Kubernetes, including scaling, multi-cloud, managed kubernetes services, K8s documentation and testing. He’s worked on implementing major managed services (GKE/AKS/OKE) in different organizations. When not coding or answering Slack messages, Saiyam contributes to the community by writing blogs and giving sessions on InfluxDB, Docker and Kubernetes at different meetups. Reach him on Twitter @saiyampathak where he gives tips on InfluxDB, Rancher, Kubernetes and open source.
We’re hiring!
We are looking for engineers who love to work in Open Source communities like Kubernetes, Rancher, Docker, etc.
If you wish to work on such projects please do visit our job offerings page.
Permission manager : RBAC management for Kubernetes was originally published in Kubernauts on Medium, where people are continuing the conversation by highlighting and responding to this story.
Mehr zu Kubernetes Services, Kubernetes Training und Rancher dedicated as a Service lesen unter https://blog.kubernauts.io/permission-manager-rbac-management-for-kubernetes-ed46c2f38cfb?source=rss—-d831ce817894—4
Neueste Kommentare